

Admiral Patrick
I’m surprisingly level-headed for being a walking knot of anxiety.
Ask me anything.
I also develop Tesseract UI for Lemmy/Sublinks
Avatar by @[email protected]
- 3 Posts
- 33 Comments
:sigh: So i’ll just put all the cards on the table here.
-
I was subscribed to the community, so it wasn’t a drive-by downvote.
-
I’m pretty positive (99.9999999% sure) language barrier was not the issue. What was stated in the comment was very clear, ignorant, and broadly stereotyping (not to mention offensive).
-
I didn’t even downvote the post. I downvoted the ignorant, broadly stereotyping, offensive comment by the OOP.
-
I didn’t even reply to the offensive comment because I don’t have time, energy, or enough fucks to give for such an ignorant take.
-
OOP decides to put anyone who downvoted them on blast.
-
OOP of that (which I am still tactful enough to keep anonymous), has DM’d me twice and insulted me.
-
OOP deletes the whole post and pops in here to play the victim. But that’s on me for letting them get away with that. I was trying to be tactful and not call anyone out when I should have taken screenshots of the whole thing.
The real Fedidrama was the drama we made along the way 😂
You can, at least partially.
If your instance is on 0.19.0 or above, you can block instances at the user level. You won’t see posts from any community there, but you will see posts from users there to communities on other instances, and you will still see comments from users on that instance.
It basically works as a “block all communities from this instance”.

 English
English- •
- dubvee.org
- •
- 7M
- •
I’ve no experience with Zerotier, but I use a combo of WG and Openvpn. I use OpenVPN inside the Docker containers since it’s easier to containerize than WG.
Inside the Docker container, I have the following logic:
- supervisord starts
openvpnalong with the other services in the container (yeah, yeah, it’s not “the docker way” and I don’t care) - OpenVPN is configured with an “up” and “down” script
- When OpenVPN completes the tunnel setup, it runs the up script which does the following:
# Get the current default route / Docker gateway IP
export DOCKER_GW=$(ip route | grep default | cut -d' ' -f 3)
# Delete the default route so the VPN can replace it.
ip route del default via $DOCKER_GW;
# Add a static route through the Docker gateway only for the VPN server IP address
ip route add $VPN_SERVER_IP via $DOCKER_GW; true
ip route add $LAN_SUBNET via $DOCKER_GW; true
LAN_SUBNET is my local network (e.g. 192.168.0.1/24) and VPN_SERVER_IP is the public IP of the VPS (1.2.3.4/32). I pass those in as environment variables via docker-compose.
The VPN server pushes the default routes to the client (0.0.0.0/1 via <VPS VPN IP> and 128.0.0.0/1 via <VPS VPN IP>
Again, sorry this is all generic, but since you’re using different mechanisms, you’ll need to adapt the basic logic.
Forgot to ask: Is your server a VPN client to the VPS or a VPN server with the VPS as a client? In my config, the VPS is the VPN server.
Not sure about the netplan config (all my stuff is debian and uses oldschool /etc/network/interfaces), but you’d need logic like this:
Server is VPN client of the VPS:
routes:
# Ensure your VPS is reachable via your default gateway
- to: <vps public ip>
via: <your local gateway>
# Route all other traffic via the VPS's VPN IP
- to: 0.0.0.0/0
via: <vps vpn ip>
You may also need to explicitly add a route to your local subnet via your eth0 IP/dev. If the VPS is a client to the server at home, then I’m not sure if this would work or not.
Sorry this is so vague. I have this setup for 2 services, and they’re both inside Docker with their own networks and routing tables; I don’t have to make any accommodations on the host.
Is there any solution (program/Docker image) that will take a port, forward it to another host (or maybe another program listening on the host) that then modifies the traffic to contain the real source IP. The whole idea is that in the server logs I want to see people’s real IP addresses, not the server in the cloud private VPN IP.
Not that I’m aware of. Most methods require some kind of out-of-band way to send the client’s real IP to the server. e.g. X-Forwarded-For headers, Proxy Protocol, etc.
If your backend app supports proxy protocol, you may be able to use HAProxy in front on the VPS and use proxy protocol from there to the backend. Nginx may also support this for streams (I don’t recall if it does or not since I mainly use HAProxy for that).
Barring that, there is one more way, but it’s less clean.
You can use iptables on the VPS to do a prerouting DNAT port forward. The only catch to this is that the VPN endpoint that hosts the service must have its default gateway set to the VPN IP of the VPS, and you have to have a MASQUERADE rule so traffic from the VPN can route out of the VPS. I run two services in this configuration, and it works well.
iptables -t nat -A PREROUTING -d {VPS_PUBLIC_IP}/32 -p tcp -m tcp --dport {PORT} -j DNAT --to-destination {VPN_CLIENT_ADDRESS}
iptables -t nat -A POSTROUTING -s {VPN_SUBNET}/24 -o eth0 -j MASQUERADE
Where eth0 is the internet-facing interface of your VPS.
Edit: One more catch to the port forward method. This forward happens before the traffic hits your firewall chain on the VPS, so you’d need to implement any firewalls on the backend server.

 English
English- •
- 2Y
- •
If you use an instance just for yourself, it doesn’t actually decrease the load on the main servers in any way.
That’s not completely true. Yeah, it still loads another server a bit, but the server-to-server federation traffic is much more lightweight than the client-to-server traffic that would be involved with you having an account on that server and accessing it that way.
But yeah, multiple, equally-sized communities on different instances is the ideal situation. The only sticky part right now is FOMO because you’d have to constantly watch for new SelfHosted communities and join them. Hopefully some frontend tools come along soon to make joining/managing multiple communities like that more streamlined.

 English
English- •
- 2Y
- •

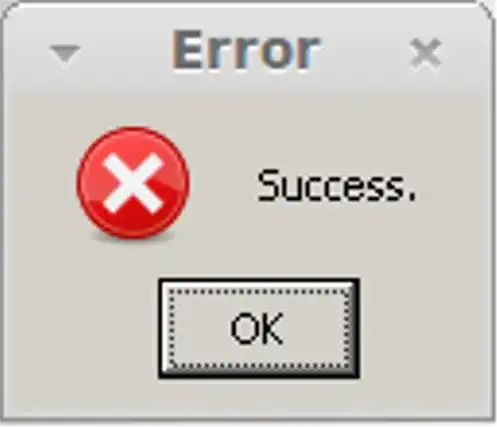


That’s literally impossible; every action taken has to be against an entity known to the instance. However, I can ban people from communities that have never posted there (which is what you’re seeing). That is to close a loophole where someone is instance banned here but can still interact with the local copies of communities on their home instance.
In such a case, those local interactions would not be moddable on that instance except by the admins. Any reports for that user would not be seen by the mods on my instance, and no mod actions could be taken by them. I think 0.19.4 or 5 addresses that, but that’s’ not the version we’re on right now, so this is how we’re handling that.